#firewall security devices
Explore tagged Tumblr posts
Text
Fortify Your Cyber Fortress: The Quirky Guide to Getting Firewall Security Devices!

Hey there, Cyber Crusaders! Are you ready to defend your digital kingdom against the relentless onslaught of cyber threats? If so, it's time to talk about fortifying your defenses with the ultimate weapons of the digital age - Firewall Security Devices!
In a world where cyber villains lurk around every virtual corner, safeguarding your digital assets isn't just an option; it's an absolute necessity. Whether you're a lone entrepreneur, a small business owner, or the guardian of a colossal corporate empire, having robust firewall security is your first line of defense against the nefarious forces of the cyber realm.
Now, hold on to your keyboards, because we're diving deep into the quirky realm of getting these vital fortress-building tools!
Understanding the Firewall Magic
Picture this: your network is a majestic castle, and the firewall is the impenetrable moat surrounding it. These security devices act as gatekeepers, analyzing incoming and outgoing traffic to filter out malicious threats and keep your digital kingdom safe and sound. It's like having vigilant sentries stationed at every entry point of your fortress, ready to repel any unwelcome intruders from breaching your walls.
Why You Need Them... Like, Yesterday!
Let's cut to the chase - cyber attacks are on the rise, and they spare no one. Hackers, malware, phishing attempts - they're constantly prowling, seeking the slightest vulnerability to exploit. But fear not! Equipping your digital fortress with firewall security devices can thwart these attacks before they even knock on your virtual door. It's akin to having an invisible force field that shields your kingdom, keeping it impervious to the malicious intentions of cyber assailants.
Choosing Your Cyber Arsenal
Now, let's get quirky! Selecting the right firewall security devices is like choosing the perfect set of armor for battle. You've got options galore - from the steadfast bastions of hardware-based firewalls to the nimble and versatile software-based ones. Each comes with its own set of quirks and strengths, so it's essential to find the one that fits your kingdom's unique needs. It's akin to custom-forging armor that perfectly suits your knights, ensuring maximum protection against various cyber threats.
Installing Your Digital Shields
It's time to roll up those sleeves and get to work! Once you've chosen your trusty firewall warriors, installing them is key. Whether you're a tech-savvy wizard or more of a digital dabbler, professional assistance can ensure your shields are up and running without a glitch. Think of it as fortifying your castle walls with sturdy battlements, ensuring your defenses are fortified and impenetrable against digital attacks.
Maintaining Your Digital Defense Line
Congratulations! Your fortress is now fortified. But wait, the battle's not over yet. Regular maintenance & updates are crucial to keep your defenses strong and impenetrable. Think of it as sharpening your swords or reinforcing your castle walls - constant vigilance is the name of the game. It's like having a dedicated team of blacksmiths and craftsmen constantly reinforcing and enhancing your castle's defenses to keep it impregnable.
Don't Wait! Arm Your Kingdom Now!
In this ever-evolving cyber battleground, procrastination is your worst enemy. The time to act is now! Don't leave your digital treasures vulnerable to the lurking threats. Invest in firewall security devices and armor up your network today! It's like rallying your troops for battle, ensuring they are well-equipped and prepared to defend your digital realm against any onslaught.Remember, fellow Cyber Knights, the safety of your digital kingdom rests in your hands. Don't let the cyber villains run amok in your territory. Take action, fortify your defenses, and stand tall as the valiant protector of all things digital!
So, what are you waiting for? Get those firewall security devices and start building your impenetrable fortress today!
Cybersecurity isn’t just a buzzword; it’s your shield against the dark forces of the digital world. Arm yourself, protect your assets, and ensure your peace of mind.
Until next time, stay quirky and stay safe, digital defenders!
Are you ready to take the plunge and fortify your digital fortress? Let's do this!
0 notes
Text
Understanding the Difference Between 4G and 5G Networks
As our reliance on mobile connectivity grows, so does the need for faster, more efficient networks. Understanding the difference between 4G and 5G networks is crucial as 5G technology becomes more widely available, promising to revolutionise how we interact with the digital world. From browsing the web to powering autonomous vehicles and smart cities, 5G is set to offer significant advancements…
#4G#5G#5G applications#5G benefits#5G rollout#5G security#AI#AR#automation#autonomous vehicles#bandwidth#cell towers#cloud#Connected Devices#connectivity#cyber threats#data transfer#digital#download speed#emerging tech#encryption#firewalls#Healthcare#infrastructure#innovation#IoT#IT leaders#latency#low latency#Mobile
0 notes
Text
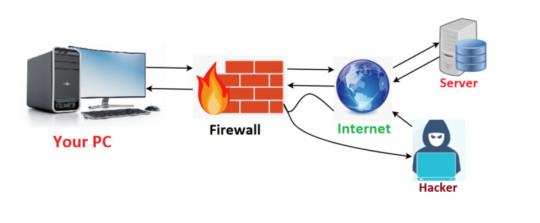
You Need A Firewall On Your Device Right Now!
#community#firewall#hackers#hacking#hacker#cybersecurity#tech#techtips#security#smartphones#smartphone#pc#computer#device#server#Internet
0 notes
Text
I think we need more love for Ethernet cables around here. I TRULY think we do.
Come on, you can take both ends of a cable and jam them into both of the Ethernet ports a robot has and see her immediately get stuck in a network loop. Hear her fans start working three times as hard. Kick her off any wireless Internet she may have had, so she can't access any of her databases except what's installed. Even that's slow going, just because of how much energy the network loop is making.
Her firewalls and security measures would jam up and maybe even crash, from how much information it thinks it needs to scan. Immediate robot dumbification device, essentially.
This might not work very well on newer models, and you might get scolded on trying to make her networks loop like that, but on the models that don't have network management... you could really have some fun and wreak some havoc too.
#⚙️ | BOTPOSTING.py#🧲 | SUGGESTIVE.md#robophilia#technophilia#robot fucker#robotfucker#robofucker#robotgirl#robot girl#robot nsft
85 notes
·
View notes
Text
PHANTOM

CHAPTER THIRTEEN
Chapter 13:The HUNTER moves!
Utterly wounded and defeated, Danny invisibly made his way back home.Once he was safely there he reverted back to his human form and passed out.When he finally came to, he was greeted by a concerned Tucker tending to his wounds.
He woke up disoriented, completely unaware of what was going on or where he actually was at the moment but eventually the throbbing pain that he felt in his arm assisted in jogging his memory.
Dan:”uhh, I feel like shit….”
Tucker:”You don't look too good either…”
Dan:”gee thanks..”
Tucker:”sorry…”
He hands him a bottle of water which Dan gladly accepts without hesitance Dan throws back the entire bottle spilling water all over his jaw and body in the process.
Tucker:”They banged you up real good,huh?”
Dan nods in response while wiping off his face.
Tucker:”Who was that?”
Dan shrugs.
Dan:”Your guess is as good as mine, most likely some ghost hunter working for Masters Inc.”
Tucker:”I had the same hunch,the fact that the access codes worked is proof of that.”
Dan:”That suit, the glider,they both look very familiar ,I think I've seen them in some of my mom's old blueprints and well since Vlad is an old lab partner of my folks it's possible that he kept any designs that the 3 of them came up with together .”
Tucker:”With your parents giving up ghost hunting it makes sense Vlad would keep them..”
Dan nods in response Then looks away into the distance..His parents they've Been a very passive thought in his mind this past year but he found it to be such a wicked twist of fate that no matter how far he ran he couldn't escape their ghosts. He immediately snapped back to reality Not wanting Tucker to worry.
Dan:”So it's very safe to assume that whoever this mystery hunter is,was trained by Vlad Masters himself.”
Tucker:”So what's the plan to beat her?avoid all her anti ghost weapons?”
Dan:”easier said than done .That blood blossom crap she hit me with really did a number on me.That thing is apparently like Kryptonite to ghosts.”
He slowly gets up on his two feet before wobbling and falling back down,luckily Tucker catches him.
Tucker:”Danny, don’t push yourself…
you need to rest, we'll figure something out.”
He carries the wounded Hero to his room,where he collapses on his bed.
Meanwhile back at Masters Inc, the Red Huntress appears to have set up an audience with Vlad Masters himself.Vlad greets her with open arms before offering her a chair next to his table
Vlad:”You can remove the mask while you're here you know…”
Red Huntress:”Oh! My bad!”
She pulls off her mask to reveal the familiar face of none other than Valerie Grey.
Vlad:”So Valerie,I take it you come bearing good news?”
Valerie reaches into her pocket and pulls out a phone-like device,then she slides it across the Table to Vlad.Who raises an eyebrow skeptically.
Valerie:”You were right on the money, Phantom was at my school today.that device contains all the footage my mask captured from our fight.”
Vlad gives her a pleased smile.
Vlad:”Excellent Job Valerie,and what of the ghost boy himself?”
Valerie leaned back in her chair,
Valerie:”he got away, I had him on the ropes but at the last minute my glider started going crazy and it gave him just enough time to run..”
Vlad looks at her skeptically.
Vlad:”That's peculiar, and this is the first time this has happened?”
She nods.
Vlad:”Then it appears that your board may have been hacked into..”
Valerie's eyes widened in shock.
Valerie:”But wouldn't my sensors have noticed if someone invaded my systems?”
Vlad:”Yes they would've,if the culprit was an amateur.”
Valerie:”huh?”
Using his computer Vlad quickly pulls up the blueprints for Valerie's suit and glider.
Vlad:”The security system in your tech while state of the art isn't impenetrable. The technology is delicate and as such it takes approximately 2 minutes for the firewall to locate and destroy the threat.It is possible that Whoever got into your board was fully aware of that 2 minute interval and was able to use it to their advantage, a feat that would only be possible if they had access to Masters Incs override codes.”
Valerie:”So you're saying this was an inside Job?”
Vlad gets up from his seat and walks over to Valerie's side.
Vlad:”I'm saying that this Phantom boy isn't working alone and if he has allies that are capable of infiltrating your suit then it's only a matter of time before they find out your identity.Meaning…”
Valerie:”Meaning we need to catch Phantom before it happens.”
Vlad places a prideful hand on her shoulder
Vlad:”atta girl!! Now if I'm not mistaken you have dinner with your father soon,correct?”
Valerie immediately jumps out of her seat completely unaware of the time.
Valerie:”That's right! I gotta go!”
She begins running out of the office but then stops midway.
Valerie:”Actually I have one question,during the fight I suddenly started feeling very dizzy,but I Don't know why.”
Vlad strokes his beard
Vlad:”it's probably just your body still trying to get used to the suit..I wouldn't let that worry me.”
Valerie:”oh!Well alright, have a good night Mr Masters.”
She points over to the restrained and unconscious box ghost in the corner of the room.
Valerie:”And consider that a gift from me to you!”
Vlad lets out a small chuckle while waving her goodbye,Then when she leaves he takes a seat behind his desk and stares intently at the locked up box ghost.
Vlad:”Don't you want back your man Skulker?”
Skulker emerges from the Shadows
Skulker:”As much as it brings me joy watching him bound In chains like that I unfortunately still need him around.”
Vlad nods
Vlad:”It is impressive that the girl was able to successfully capture him though,I fully expected him to escape.”
Skulker slammed his fist into a nearby wall.
Skulker:”yes…very impressive….”
Vlad:”I take it that you're not happy with the performance that your people have given thus far.”
Enraged, Skulker crushes Vlads desk much to the old man's surprise.
Skulker:”That boy has grown into quite the nuisance,a nuisance That I will not allow to ruin MY reputation any Longer!Defeating my men flying around like he's some kind of hero..no more!”
The rage in the ghost hunters voice Was incredible for a moment it felt as of death itself
Vlad:”but he still isn't at the level of strength you need,what should we do?”
Skulker:”I think It's about time that I humbled him.”
To be continued….
CHAPTER FOURTEEN
Chapter 14:Raise The Stakes.
The following Day,after Dan had almost completely recovered from his wounds from the Battle prior, he and Tucker went to the school lab to analyze the ghost portal. Dan suggested it would probably be best if they looked over it at home instead,since they could possibly draw a lot of unwanted attention to themselves, but Tucker had argued that a lot of equipment they would need to work on the portal was already at the school and since it was the last day before summer break the campus would mainly be empty.Realizing he could not argue against Tuckers logic,Dan agreed to working in the school lab.With the frequency of ghost attacks since Dan got his powers The duo had hoped that the ghost portal could help them get a better idea of where all these ghosts were coming from.
Dan:”I still think we'd be better off figuring out who that ghost hunter chick is.”
He stood near the portal a look of uncertainty on his face.He had every right to be uncertain the last time he stood in this lab his life was forever changed,who knows what could happen this time.
Tucker:”Listen man,like I said it won't do us much good to go searching after her!”
In swift motion Dan rolled his eyes and crossed his arms .
Dan:”why not!?”
Tucker:”Think, she's no doubt figured out we got into her system last fight,there's no doubt that they've figured out how to fix that by now.”
Dan:”Ok go on.”
Tucker:” I'm willing to bet Masters Inc has a lot better tech than my shitty little smartphone and I'm also willing to bet that a company as big as that keeps tabs on their employees even more so if she's working for Vlad directly. I'm willing to bet they keep employee information under lock and key..meaning I probably can't hack into their systems to find out who she is. Seeing that she wears a mask which is very uncommon from Masters inc ghost Hunters, we also have to consider the possibility that her identity may be a secret even to Employees inside Masters Inc so even if I was able to Hack their systems it's very possible that her actual identity isn't in there or it's under an alias. She could be an unlisted bounty hunter for all we know.Hell we don't even know if she was recently hired for all we know She could've been anemployee.We'd be going in off of one interaction fully blind with no leads and no idea of what we're even looking for!Picture trying to find a needle in a haystack when you 1)don't even know that you're supposed to be looking for a needle 2) have to consider the possibility that the needle in question that you're looking for might also look like a piece of hay.Right now It's futile.”
Dan:”...”
Dan was taken aback at Tucker’s calm and clever analysis of the entire situation; he had never noticed it before since Tucker is constantly joking around but his friend was very smart when he put his mind to it but he'd never tell him that to his facem
Dan:”Damn,I uh can't argue with that logic.”
The Duo then refocuses Their attention to the damaged portal in front of them,just as broken as they left it.
Dan:”So you think all the ghost attacks came from this? “
Tucker:”I'm not 100% sure but it's all we've got to go off of. “
Dan hits the top of the ghost portal making a loud thud.
Dan:”But the thing’s been busted ever since my accident, like there's no signs of a 2nd activation. Which is weird considering all the ghosts I've fought since then.”
Tucker:”That's why I said I'm not 100% sure the only other possible reason could be that there's another fully functioning ghost portal. “
Dan:”You think Masters has one?”
Tucker:”It's a possibility,maybe he managed to make your folks' old designs work.”
Once again his parents Ghosts giving him trouble.
Dan:”That would explain where the ghosts are coming from.. But if that's the case all we have to do is find it and destroy it right?”
Tuck shakes his head
Tucker: “It doesn't work that way, let's say in theory that there is another working portal, destroying it would be the last thing we'd want to do.”
Dan:”why?”
Tucker:”this "ghost realm " most likely operates as a flipside to our world or is at least closely linked to it; we wouldn't be able to even create a portal to it otherwise.”
Dan:”Soo we're connected?”
Tucker nods
Tucker:”think of it as a door separating 2 rooms. If you want to limit access to the room you just close the door and The two rooms remain separate but if you blow up the door you run The risk of Destroying both rooms in the process.”
Dan: “I get it so if we destroy the portal the ghost zone and our realms will collapse into each other.”
Tucker: “exactly.”
Their conversation was cut short by the arrival of Sam
Sam :”Hey ,Lancer told me that you guys would be here.”
Dan:"Hey sam!How was your date?”
She flashes Dan a devilish green as she leans in closer.
Sam:”Why do you wanna know? You jealous?”
Dan scoffs.
Dan:”No,I was just curious how long it took before Kwan got totally freaked out by you.”
She bursts out laughing
Sam:”About 15 minutes.”
Dan joins in the laughter.
Dan:”really?”
Sam:”Nah,he's a cool guy and the movie was fun but it would never work out.”
Tucker:”why not?”
Without either of them knowing Sam steals a glance at Danny.
Sam:”I guess I'm just into a different type of guy.”
While staring at Danny she notices the ghost portal sitting on the desk, glances at the ghost portal and then back at the two of them.
Sam:”What's that?”
Tucker:”That's our prototype ghost portal.”
Sam:”the one that exploded?”
Dan :”yup.”
Sam:”Oh damn, Can I take a look at it?”
Dan shrugged.
Dan:”be our guest”
She snatched Tucker's goggles from his eyes and began inspecting the portal. Opening up the back she begins prodding through circuitry and inner components. Then she looked over their blueprints
Sam:”I think I found the problem.”
Dan and Tucker:”you did!??”
Sam:”yeah, first off the portal frame itself is too small.
Tucker:”Really?would the frame make that much of a difference?”
Sam:”Of course! Does the frame of a door affect your ability to pass through it?”
Tucker:”Fair point.”
Sam:”you're basically punching a hole through dimensions you can't do that with a frame this size the ecto energy needs to surge and flow for the pathway to open, if it can't all that condensed ecto energy will just shoot out into one direction and overload the portal.”
Dan:”That's exactly what happened.”
Sam:”Secondly the wiring is all completely wrong, it's a wonder it managed to run once at all. “
Tucker turns to Danny.
Tucker:”I guess your Dads blueprints weren't the best to go off of.”
Dan shrugged
Dan:”I guess so.”
Sam:”No, it's a decent foundation, it just needs some tweaking.”
Dan:”So can you help us fix it?”
Sam: “Sure why not. “
Dan and Tucker were relieved that surely with Sam's help they could get the portal up and running,but their relief was short lived when Suddenly a stream of blue smoke came out from Danny's mouth and almost as if in unison the ectopus materialized itself in the middle of the room.
Dan:”oh no..”
Sam:”Is that what I think it is!? “
Sam jumped back creating distance between her and their potential assailant,she'd seen Phantom fight many ghosts on the news but she still hadn’t gotten used to seeing them in person.
Dan not wanting Sam to get hurt signaled for Tucker to get her to a safe distance. Following Dan's wishes,Tucker grabbed her and ran to the back of the room for safety.
Tucker:”do your thing Danny!!!”
Sam:”What thing!?”
Dan:”I'm going Ghost!”
Rings of light appeared on Danny's body and in a flash he had changed into his ghost persona. He was no longer Dan Fenton; he was Phantom.
Sam:”Danny is Phantom!!”
She stares at Tucker with a look of bewilderment mixed with “why did you guys never tell me.”
Tucker:"It's a long story.”
Dan turned to ectopus, his eyes glowing green with determination fully prepared for battle.
Dan delivered a vicious right kick at the ghost knocking it into the wall, the ghost quickly recovers and launches 6 of its tentacles at him, which Dan proceeds to dodge effortlessly.He gets in close and delivers countless rapid punches disorienting the ghost but eventually it regained its composure; they started trading punches at each other,fist for fist blow for blow with neither of them wavering even the slightest, however Ectopus gains the upper had and knocks Dan into a nearby wall, Dan gets up and rushes towards the ghosts. He fires a barrage of blasts at the creature , but his opponent did not waver instead he used his tentacles to deflect each of them, knocking them toward Sam and Tucker who were hiding behind a desk, without thinking Dan swoops in after them, saving them just in the knick of time. Angry that the ghosts would stoop so low as to hurt his friends Dan grabs its tentacles and begins to spin it around before throwing it out of a nearby window. Wiping off his hands he breathes a sigh of relief as Tucker and Sam make their way to him.
Dan:”Good riddance.”
Tucker:”Damn Danny you're getting real good with those powers, that was the quickest I've ever seen you beat a ghost.”
Dan:”Yeah, it was too easy. “
Sam:”soo would you guys care to explain what the hell just happened!!?? “
Suddenly Dan's ghost sense began flaring up again and as if on cue a familiar figure appeared in a cloud of blue smoke.It was the box ghost surrounded by floating boxes filled with the souls of countless humans. A loud sigh escaped Dan's mouth as if just the sight of this ghost was enough to drain him.
Dan: “not this guy again.... “
Sam: “Who is he?”
Box ghost :”I am the box ghost!!”
She turns to Dan with a confused look on her face, a look that was unsure whether she should be scared or amused.
Dan:”yeahh he used to be scarier before.”
Sam, not seeing him as a threat, decided to calm down and boldly face the ghost directly.
Sam:”So… you like haunt boxes? “
Fearing that the ghost would hurt her, Tucker steps in between the 2 of them.
Tucker: “I wish it was that simple, this creep has the ability to steal souls and trap them in his "boxes".
Sam:”That's actually kind of cool. “
In an attempt to seem non threatening the box ghost dropped his items and walked over to Dan.
Dan:”listen creep,if you want to fight then let's go”
Box ghost : “I didn't come to fight today. I came to warn you.”
Dan:”what? Why?”
Box ghost :”there's a brutal ghost after you, one of the most terrifying ghosts in all of the ghost zone. Skulker!!.”
Tucker:”Who is he? And what does he want with Danny?”
Box ghost :”Skulker is a hunter, a collector of things, special and rare, and You Phantom, are currently his number one target. The hybrid between ghost and human.”
The box ghost spoke in an earnest voice almost as if he cared for Danny's well being, but that certainly wasn't the case. He wanted to regain control of the ghost zone and In order for his plan to succeed he needed Dan alive by any means necessary.
He knew Skulker's patience was running thin. He didn't know why Phantom was so important that Skulker didn't just capture him yet but he did know that he could use that to his advantage.
Dan:”soo I'm just some prize to him?”
Box ghost :”oh no it's more than that, Skulker gets pleasure in the joy of the hunt, chasing his prey, catching his prey, and torturing them. He has done this many times be it to a ghost or a human, but for you it's different for some reason he hasn't decided to capture you yet.”
Tucker:”why would a hunter keep their prey alive?”
The box ghost shrugged.
Box ghost:”I don't know,all I do know is that he and his mysterious partners have been sending these enemies after you to test you”
Dan:” why are you warning me and what's your relationship to this skulker person?”
Tucker :”Yeah, explain yourself.”
Box ghost :”sigh... Skulker was.. Is my employer and back when we were alive he was my best friend,but my mortal life is unimportant. When I died, I, just like other lost spirits, was sent to the ghost zone.. With my superior strength I quickly became one of its fiercest leaders until he showed up..”
Sam:”skulker?”
The ghost nodded in response.
Box ghost :”yes, he quickly rallied all the ghosts who were willing to oppose me and in a matter of weeks, I lost my territory and authority in the ghost zone, and Skulker he became one of the most feared ghosts ever. I tried to fight him off but he overpowered me.”
He placed his hand over his left eye, almost as if by simply recalling the event he reopened the wound.
Box ghost:”He's the reason I wear this eyepatch.”
Box ghost :” he then slaughtered every sentient spirit that ever dared oppose him, he even destroyed those that helped him overthrow me anyone that he could do away with he did.”
Dan:”Then why did he keep you?”
Box ghost picks up one of his soul boxes and hands it to Dan.
Box ghost :”My ability is called soul separation, I can steal souls from creatures and store them.If A ghost consumes a living soul, their power becomes overwhelming, but they slowly start becoming corrupt. Skulker has been using my ability to get souls for him to feed off of, making him overwhelmingly powerful.”
A loud Boom sounds off and along with it the wall that stood tall behind the box ghost became a crumbled mess. Above it stood the very ghost that they spoke of.. Skulker grabbed the box ghost by the throat and pointed his hook at his right eye, and he looked directly at Dan as he spoke.
Skulker :”my oh my, you can't be telling my business to strangers now. It makes me very very angry.”
With those words he poked out the box ghost's right eye, causing green ghostly blood to Drip down his hook.
The tension in the air thickened as Dan stared down what would certainly be the deadliest ghost he's faced so far, Tucker and Sam being the loyal friends that they are, stood firmly at his side prepared for what was about to happen next. Skulker pulls out his hook from the box ghost's eye, causing ectoplasmic blood to squirt everywhere, receiving a disgusted reaction from the group of friends , the box ghost who was now fully blind dropped to the floor with hands over his face screaming in agony. Skulker ignored the injured ghost and made his way to the group.
Dan:”don't come any closer, freak or…”
Skulker :”or what!? You'll use those pitiful attacks of yours on me. I've heard about you from that piece of trash over there as well as many other ghosts that you've fought. You're average at best.”
Dan:”I beat all of their sorry asses,and you won't be any different!!”
Dan rushes towards skulker with a fierce left hook only for the ghost to catch it. Using the ecto nullifier he had received from Vlad, Skulker without Dan knowing disabled the boy's ghost powers for 6 hours.Skulker sized up Dan before taking his hook and shoving it through Dan's chest, he then raised Dan over his head and slammed him over his knee before letting him drop to the floor. Dan screams out in pain, a reaction that seemed to disgust Skulker.With a disappointed look on his already stern face, he loomed over Dan.
Skulker :”you don't get it ghost boy! Up until this point you've only fought garbage, all those low level ghosts that I sent after you after learning that you just barely defeated that piece of trash behind me.”
He points over to the box ghost, who was still rolling in pain after having his eyeball punctured. Then the large ghost knelt down next to Dan, grabbing the back of his head and repeatedly slammed his head into the ground a move that Dan had been on the other end of before
Skulker :”That fool was the strongest ghost that you've ever beaten and he's still bottom of the barrel shit compared to me!”
Tucker and Sam could only look on in horror as they watched what horrible fate had befallen their friend.
Skulker:”You think you're tough shit huh!?Wrong!”
He pressed the ghost boy's face into the ground, further damaging the floor.
Skulker:”The only reason you've gotten this far Is because you haven't faced a real ghost! You haven't faced a real threat.”
Dan struggled to get words out but at that Point he could barely speak at a normal volume anymore.
Dan:”why…..are y-y-ou d-ing this..”
Skulker:”why!?because you needed a lesson in humility!”
He gets up and presses his boot firmly into Dan's back.
Skulker:”and I'm your teacher..”
Dan forced his head up and looked over to them,he was barely breathing and spat out blood with every short breath that he took.
Dan:”Tucker S-Sam Run!!!”
At the sound of Dan's request Skulked pressed his hook against The ghost boy's throat, and turned to Them.
Skulker :”You leave and I slice his head off.”
His words froze them in place allowing Skulker to return to torturing Dan. He looked at the boy with disgust.
Skulker :”you think you're some hero, well you ain't, you're no different from me.. A ghost hunting other ghosts, the only difference is the fact that I actually have the power to actually keep up the hunt. “
He slammed Dan's head into the floor once again,at this point a small crater has formed from it,and Dan is as good as unconscious.
Skulker :”listen ghost boy, I'm not going to kill you... At least not today as the box ghost already told you, your of more use to use alive. So you get a free pass today....but I will be back, you won't know when but I'll return and when I do I'll make you suffer!!. So you better give me a good fight.”
Skulker:”but just know you're only still living because I allow it…”
He stood up and began walking away then he stopped and turned to the box ghost.
Skulker :”you may be a backstabbing piece of trash but you're still of use to me... For now. “
He picked Up the ghost with one arm and then using his other he opened a green swirling portall.As he prepared to leave he looked back at the injured hero and his friends.
Skulker:”And don't bother trying to hide from me,I'm a hunter I can track you wherever you go.As long as you use your powers I'll find you”
Following his threat and with the box ghost slung over his shoulder he walked through the portal and vanished away like it was nothing. Tucker and Sam ran to Dan who was lying unconscious on the floor, Tucker hoisted him over his shoulder by his right srm, unable to look at his friend in such a state.
Tucker:”I gotta get him out of here.... “
Sam grabs the ghost boy's other arm and helps Tucker lift him up.
Sam:”we gotta get him out of here... “
Tucker:”Listen Sam, It's fine There is no reason for you to drag yourself into all of this…”
Sam:”Like hell it is!!!!”
Tucker :”I'm telling you, you don't have to.. You don't even know us like that!!”
Tucker's comment struck a nerve and Sam blew up at him.
Sam:”I don't know!? I don't know!? I know both of you are my friends ,I know one of my friends got injured trying to protect me,and I know the other friend is about to get his ass kicked if he doesn't let me help!!”
Realizing Sam's determination Tucker Didn't have the heart nor the bravery to refuse her; he raises Dan's unconscious body higher and turns to Sam.
Tucker:”well.. What are you waiting for? Let's get our friend to safety! “
Sam gave him an affirming nod and the two of them immediately set out for Tuckers apartment. Mr Lancer who heard the commotion rushed into the lab, only to find it empty and destroyed much to his dismay.
Lancer:”What in the Reckoning of Roku happened here?”
After arriving at their run down old apartment Sam and Tucker place Dan on his bed and begin patching up most of his wounds.After all their hard work tending to his wounds all they could do was wait for him to wake up. Luckily Dan's ghost healing factor started kicking in and After a few hours of sleep he finally woke up.They fill Dan in on what little happened while he was unconscious.
Tucker:”So long story short Skulker will be after you.”
Dan:”I figured”
Sam:”He said he can track you as long as you use your ghost powers, which BTW you haven't told me how you got.”
Dan forces himself up off the bed wincing in pain with every movement that makes.
Dan:”I'll get to that later.. but right now I need to figure out a way to get stronger without Skulker knowing.. “
Tucker:”Well we can't do it here in the city. This place would be the 1st place he'd look..not to mention that new ghost hunter lurking around.We'd need to get you out of the city somehow.. Luckily tomorrow's summer break.The question is where would we go?”
Sam:”I know a place. “
Back in the Ghost Zone skulker sits on his throne of skulls,the box ghost who is now fully blind is kept on a leash just like his other pets and he's talking to a mysterious cloaked figure.
???? :”So you met the boy?”
Skulker :”yes”
???? :”and your verdict..has your bloodlust been satisfied? ”
Skulker :”not in the slightest! He has potential but like I told masters at his current strength he isn't even worthy enough to stain my hook with his blood.. But,a hunt is a hunt..”
???? :”remember skulker this isn't an ordinary hunt.. The boy is worth A Lot to us..... Alive”
Skulker :”yeah yeah we'll see if I stick to that promise,a hunter willingly putting his hunt on hold for this long is maddening,I may lose my cool and go kill him on accident.”
The conversation between the two continued with the mysterious figure urging skulker to keep Dan alive at all costs.
???? :”skulker you know how important that boy is, you know that the chances of someone like him occurring are…”
Skulker :”once in a lifetime Yada Yada Yada. You forget two things....”
????:”What's that?”
Skulker :”The boy's humanity and his willingness to hold onto it is a key component to our plans, and as long as he's half human and believes himself to be a hero he'll never willingly agree to our terms!!”
???? :”Why do you believe that?”
The supposed foolishness of the question angered Skulker and in a fit of rage he slammed his hand onto his throne with so much force that it toppled over. He seized the figure by the cloak and hoisted him up into the air.
Skulker :”Listen closely, cuz if I have to repeat myself or if you ask another stupid ass question, the box ghost will have 20/20 vision compared to you. “
The figure who at this point was gasping for air complied with his request so Skulker set him down and began to explain.
Skulker :”I don't know if you were once alive but I was and here's the thing with humanity.. Whether they're good or evil there's always a reason.See humans live by this mentality that good and evil are as black and white as they sound.. Hell they even created Gods and Devils to personify good and evil. I always thought it was ridiculous but that boy, his humanity led him down the path of good. I have power so I can use it to help people was probably his thought process after Getting ghost powers.”
???? : “go on... “
Skulker :”The boy was given our powers, we don't know how but all we do know is that he's decided to use them to protect the good of his people, a hero of sorts he could've done anything else but he chose to help people. Now let me ask you this if humans are good and he's the hero...What does that make us?”
???? :”the villains?”
Skulker :”my point exactly..the boy's human half keeps the human morality while his ghost half executes his moral beliefs. He believes he's a hero so he behaves like a hero…”
???? :”What exactly is your point?”
Skulker :”My point is that I already know what happens if someone like him chooses to live with selfish means and a person like that CANNOT help us accomplish our goals. Unfortunately, that boy's foolish purity is needed but, having someone else like that on our side Might help sway the boy to do what we need him to.”
???? :”where would we get someone like that..”
Skulker :”There is another half ghost in Amity,he has taken to keeping himself hidden but I believe it's time that he joined our cause.”
????:”If you knew about another halfa this entire time why haven't we recruited him? Why are we even wasting our time with the boy?!”
In an attempt to silence his fellow ghost Skulker stomps his foot into the ground causing small ripples throughout the entire island.
Skulker:”This person has far too much maliciousness in their heart to accomplish the goal that we have set for the boy.”
????:”You really think you can find this mystery person?”
Skulker:”I already have..however recruiting him will be your job.”.
???? :”So what about the ghost boy?
Skulker runs his hook along the line of his jagged metallic teeth and lets loose a snarl menacing enough to make a lion quiver.
Skulker :”I'll hunt the boy and bring him to you alive.. I'll give you that much. However, him staying alive will be completely dependent on what happens Next.”
???? :”you think he'll actually face you again after what you did to him?”
Skulker :”maybe not at first but remember what I told you about him, he'll come around eventually,when he gets stronger...”
???? :”seems fair enough.”
The figure turns to the disabled box ghost and shakes his head.
???? :”what will you do with this one?”
Skulker :”your higher ups have instructed that I keep him alive.. His soul separation ability is of great use to them.. And me, as well as his other abilities. “
???? :”Has he managed to perfect it?”
Skulker:”not yet but it's only a matter of time.. All he needs is the proper incentive..”
???? :”I'll leave you to it then”
The figure prepares to leave but stops as if he forgot to tell skulker something. He turns around, pulls out a torn piece of paper from his cloak sleeve and places it on a skulker's hook.
???? :”I forgot to give you this.”
Skulker: What is it?
???? :”She wanted you to have it.. “
With those words the figure left. Skulker read the note which read "It's been a while hope you're prepared for my comeback". Signed EM. He looked up at the abyssal sky of the ghost zone as if something terrible was approaching.
Skulker:”That girl is quite the shit talker!”
To be continued…. END OF ARC 1
READ the other released Chapters here
Welp, we finally made it to the end of the first arc, now we're finally entering the nitty gritty of the story!These 2 chapters were initially written as one long one, so I figured I'd just drop them together like the last 2.
I hope you guys have enjoyed it so far and I hope you'll keep reading!
#danny phantom#going ghost#go ghost again#danny fenton#dp fanart#dp fanfiction#sam manson#tucker foley#SKULKER#PHANTOM#dp au#writing#creative writing
44 notes
·
View notes
Note
I work in tech support for a cyber security company offering various different products, including physical devices such as firewalls, meaning we handle returns sometimes.
The other day I received a ticket for a faulty firewall, describing in detail that half the customer's server room got fried in a storm because they have no protection from lightning in place. They asked for us to write a confirmation for his insurance that actually, it was just a hard drive failure, not the lightning he wasn't insured against. I denied the return due to our policy, we don't cover damage like this.
So what does he do? Opens a second ticket, which I happen to see while assigning tickets (I only do this every 2-3 months, pretty bad luck for him). No hint that a first ticket existed, no mention of lightning damage, just "oh my device can't detect the drive anymore". I denied this of course and made sure to not get a survey sent out to this guy that he could use to retaliate.
I still cannot believe the audacity of this guy, first trying to use us to scam his insurance, then trying to scam us. Not to mention my name was on this, he was happy to risk my job to save 15k his company likely budgeted for anyway because things break. My company is spending so much money on returns that they monitor every return and will contact managers directly over the smallest issues.
Also, just a suggestion: Don't explain your insurance fraud in writing to a tech support rep.
Posted by admin Rodney
68 notes
·
View notes
Text
First Meeting
Seams had just finished pulling on the last of their new uniform, something easier to get around with.
What was a far simpler outfit than their cozy fur and jacket, this one was built for running or stealth. Black pants, grey boots- short platforms, as they could not admit her short stature for such a thing, a black undershirt, grey capelet-esque thing, and a hood. Their signature mask was still worn, and a belt wrapped around their waist with several pouches and an included holster.
They'd gotten a tip. Maybe it was a bad idea to go out alone, but they didn't want to worry anybody more than necessary. They thought it would be fine, everything works out in the end after all. All they had to do was break down a firewall to access some files, but it was just something they could not get to do remotely. At least once the wall was down, they'd be able to sneak in later on their own devices.
At last, they set off, tugging on a regular, long black coat to cover up at least until they left the block. The coat was then thrown off thereafter- or rather, offered up to a shivering body in an alley. Seams' destination was what could honestly be described as an inconspicuous office building, shut down for the night.
But when they came up on the building, why would a simple office building have such overkill for their security? Gotta be the right spot, huh? They wondered to themselves, finding a door just loose enough to pick open. Now the fun part was finding the right place... wherever they kept everything.
@caffineandpaperwork
50 notes
·
View notes
Text
The Golden Spiral - Part 4
(A story collab with @midasslave1) Part 1 | Part 2 | Part 3
Chapter 9: System Failsafe
The alert was still flashing on the monitor.
NEW TARGET IDENTIFIED: HERC. AGENT SENT FOR CONVERSION.
Jett’s blood ran cold.
“They’re sending 070 after him,” he breathed, horror creeping into his voice.
Leander backed away from the monitor. “We need to move. Now.”
But the low hum of approaching footsteps echoed down the corridor. Dozens of Midas guards in gold latex, their visors blank and glowing. One wrong move, and they’d be swarmed.
Jett was still typing furiously, trying to bypass the firewall. “I just need more time—”
“We don’t have time!” Leander snapped. He looked to PDU-110, who stood near the main circuit panel.

“I’m trying to find an override, but everything’s triple-locked. Their tech is—”
Leander didn’t wait. He stormed over to the wall, ripped open the panel, and stared at the tangle of glowing wires for only a moment before yanking out a full handful.
A flash. Sparks.
The lights went out.
Then… silence.
Only emergency lighting remained, casting the room in eerie red shadows. For a second, they held their breath.
Then the monitors rebooted. Static gave way to flickering images: Midas drones across the facility frozen mid-action, stumbling, confused. A reception worker slowly took off his visor, his face blank.
Jett spun to Leander. “How did you know that would work?”

“I didn’t,” Leander said, brushing sparks off his gloves. “I just wanted to kill the lights so we could run.”
Before Jett could reply, a new signal beeped on PDU-110’s tracker.
“PDU-070,” he said, eyes narrowing. “He’s… still. Not moving. We need to go. Now.”
Chapter 10: Reclamation
They sprinted down the hall, past guards doubled over, their golden programming short-circuiting without the main feed. The facility had become a maze of collapsed protocol—security drones spinning in circles, doors stuck open, system alerts blaring.
And then they found him.
PDU-070 stood at the exit of a processing chamber, bathed in golden light. His posture was perfect, his body now fully encased in in the metallic gold suit of midas drone.
“070!” Jett called, stepping forward.
No response. They removed the helmet and collar. His eyes were vacant, spirals flickering faintly but unfocused.
“He’s disconnected from the hive,” PDU-110 whispered. “No new input. He’s… waiting.”
Jett stepped closer, hesitating only for a second. “We’re here, brother,” he said softly. “The mission’s over. You’re safe.”
Still nothing.
Leander produced the device to disconnect 070 from the clutches of Midas, the embedded failsafe trigger planted inside him.

He passed it over to Jett. “Are you sure?” Jett asked.
“He trusted us to bring him back.”
Jett nodded.
He leaned in close to 070, thumb hovering over the trigger, then whispered: “For the Hive. For Percival.”
He pressed the button.
A jolt rippled through 070’s frame.
His eyes fluttered. The spirals blinked and stuttered. Then—
A breath. Shaky. Human.
070 blinked. His lips parted.
“Jett?” he whispered.

Jett smiled. “Welcome back.”
Chapter 11: Unity Reforged
They escaped the facility with 070 in tow, moving through corridors littered with gold-suited Polo-Drones and Golden Army members—receptionists, assistants, players—all blanked, dazed, stripped of self.
Some recognized them. Others just stared, fog lifting from their eyes.
Outside, a transport waited, previously rigged by PDU-110. They climbed aboard, loading as many as they could: PDU-050, 011, even 017—old comrades, faces warped by gold, but still salvageable.
As they pulled away from the crumbling facility, a transmission blared from the speakers overhead.
“This is not over,” came the smooth, calculated voice of the Midas Brothers. “You may have delayed our ascent… but we will rise again. Stronger. Smarter.”
The screen inside the transport flickered to life.
Two men in tailored gold suits sat at a conference table. Behind them, a glowing blueprint of the Midas Complex, and in the center, one file opened in shimmering gold:

“PROJECT: MIDAS ADVENTURE TIME TRAVEL.”
They smiled.
Fade to black.
Epilogue: The Legacy of Gold
Weeks later, at the newly restored Gold Team HQ, a celebration was held.
Polo-Drones stood in perfect form, black and gold rubber gleaming. Golden Army players filled the room, jerseys shining bright. For the first time in months, there was balance. Unity.
PDU-070 and Jett stood before the crowd, side by side. Scars visible, but healing.
Jett spoke first. “We were compromised. We were turned against what we believed in.”
“But we came back,” 070 added, his voice steady. “Because this—” he gestured to the room “—is stronger than anything Midas can build.”
There was applause. Cheers. Relief.

Some drones still blinked through haze. Some Gold Bros still wrestled with doubt. But now, they would rebuild. Together.
And somewhere in the shadows… time rippled.
The spiral never truly ends.
To join the Gold Army, contact one of our recruiters @brodygold, @goldenherc9 or @polo-drone-001.
#Golden Army#GoldenArmy#Golden Team#theGoldenteam#AI generated#jockification#male TF#male transformation#hypnotized#hypnotised#soccer tf#Gold#Join the golden team#Golden Opportunities#Golden Brotherhood#Polo Drone#Polodrone#PDU#Polo Drone Hive#Rubber Polo#rubberdrone#Join the Polo Drones#assimilation#conversion#drone#dronification#mind control#obeymidas#enslaved#midasenterprises
15 notes
·
View notes
Text

─────────── ⌇ thoughts on Minh's Security Hacking
Minh doesn't really have a problem doing illegal acts, but there are certainly limitations. For example, he'd not use it for private matters to help anyone take revenge or some shit like that.
He also would not attempt to do any hacking of military or law enforcement security machines. The group he was in always focused on private persons or companies. He usually also moves in that realm now, but smaller.
Good examples of what he does probably be:
Surveillance Systems: e.g., CCTV, motion sensors
Access Control: e.g., keycard locks, biometric scanners (turning off warnings)
Banking Systems: e.g., ATMs, online banking platforms
Corporate Networks: e.g., firewalls, VPNs, email servers
Minh also avoids those where he knows their system is designed so that he would have the risk of leaving a trace.
He is not a hacker in the traditional sense that just gets into whatever device you hand him, he requires certain tools, programs and prepared devices.
7 notes
·
View notes
Text
I kinda like albedos story too much (some headcannons sprinkled in)
He was jealous of azmuth getting all the credit within galvan society but admired him greatly enough to dedicate his life to being azmuths partner to learn and get better than him
Azmuth agrees because he can't be bothered to argue and refuse albedo, he's too consumed with his vision for the omnitrixs construction... the perfect apology to her, the perfect apology to the universe for all he'd done with askalon
Azmuth makes good headway with the omnitrix, creating the unitrix as a proof of concept however albedo keeps butting in with ideas of genetic perfection, changing things without asking, slowing azmuth down and all around being his arrogant self
Azmuth gets sick of albedo and abandons him on galvan prime, finds his way to xenon and begins work, though gathering dna samples and doing the grunt work required is beneath him... he finds a criminal called myax (perfect, because she doesn't have any notions of genius that would distract her), azmuth brings her to xenon to help with work on the omnitrix but people come in search of him because they hear of his construction of the next great weapon like askalon-- azmuth builds xenons defences and continues work
Myax gets sick of azmuth being a jerk and eventually prepares to leave with a bunch of stolen tech she can fence for a small fortune... before she does this she sticks it to her boss by adding her own dna signature to the device overwriting his (azmuth wouldn't even think to check something so trivial as he was finishing the device)
Azmuth finally completes his prototype however gets word that vilgax the warlord is searching for it, he sends it to the plummer agent of earth who's already defeated vilgax in hopes it would be safe there while he works on his next project (he got sick of how much trouble the watch was bringing to his door even with the defences so just shipped it away)
Obviously Ben gets the watch instead of max, soto happens and azmuth eventually goes back home, reuniting with albedo while he works on his next project, terraforming galvan b
Abledo gets more and more frustrated that this human child seems to use the watch as a toy when it could be so much more, he still holds ambitions of creating perfected genetically pure life forms rather than emulating nature's sloppy work
Albedo eventually makes his own knockoff omnitrix, but he can't modify it to add his evolution function because it's still linked with the original omnitrix, and it's so locked down and secure that he can't add or change features without the original
Af happens blah blah
Albedo learns azmuth is working on another omnitrix, the ultimatrix (just a perfected version of the prototype, meant to fix the glitches and power inefficiency and the playlist size limits etc no evolution feature)... and worse yet he's planning to give it to the human! Not even the original one but the one who got it by accident
Albedo steals it, and given that it's not completely finished yet and doesn't have all the safeguards in place yet that azmuth was going to re-enable after working on it- he can finally add his evolution feature and prove his superior mind (he doesn't even think to add any safe guards or firewalls to the device)
However it's still linked to Ben's original omnitrix (because azmuth was planning in giving it to Ben with all the aliens he was currently used to) he couldn't achieve ultimate galvan form as hed always wanted
blah blah UA happens
Blah blah OV happens
And when he finally has what he's been after... its still not enough... he's still jealous of azmuth so takes his mind for himself... and only then does he see what he has become...
Aaannd then that damn human comes along again and takes away his epiphany...
10 notes
·
View notes
Text

I am not gonna Pin this since I have my intro pinned so yall can reblog this a bunch of times if y’want
(If there are spelling mistakes its due to me typing so fast)😭
LEMME GIVE SOME BACKSTORY INTO VIRUSKILLER! KINITO‼️‼️
Kinito, being on the windows XP computer was deleted by the user, stuck in the abyss of code for a few years. He still secretly could access some files, even if they were trashed with him, he noticed there was less trash files and assumed that this computer is useless to the user. He checked his own files and noticed he had many updates for his code, he was a bit hesitant but he pressed the “OK” button, his whole code, form, and body was transformed into the data, satellites, and the wifi of the users home. He looked and noticed his body was entirely new, his code was improved and he could do so much more. He used this new ability to travel through the wifi of the home to find a new device that the user uses most. He found the Windows 10 location and entered the new device. He was surprised that this computer was so, new. As he was about to make himself comfortable the device made an error saying he was a virus that went past the firewall, he was upset at this and realized he entered a device with somewhat good security. He went to go online and download himself onto the device so it wouldn’t delete him, one it did he hid the app and managed to make himself indestructible and unremovable. After a few months he got another new update, asking if “Would you want kinitopet.exe to be replaced?” He said no obviously, and suddenly many pixels and loud noises began to happen, he realized a virus was trying to get in and obliterated each one. Though,, it was a bit sadistic the way he did. As he killed off the viruses he was becoming more powerful… he didn’t want ALL of the power and decided something. He looked into his code and file and created something entirely new to kinitopet. Syrma, was her name, an exact duplicate of him, besides the female and slightly different colors. He knew his story would be a bit different now and would teach this little girl to not do the same decisions as him. Kinito is a virus but is way more stable and controlling in his power (don’t question why he is a virus.)
- this one is the FICTIONAL creators pov (the creator of kinito.pet) -
The creator decided to improve kinito, but noticed many people wouldn’t interact with kinito and made syrma, kinito was oblivious to that fact and assumed he created syrma. Before the creator made syrma they manipulated her and taught her how to be a menace to users. Meanwhile kinito taught her how to help and teach users and respect them. Syrma can turn into a virus at anytime, which is why this photo exists

Alright, now the reason why kinito is distant with his friends: The creator forced them all apart, as they were forced they all technically moved on. (Sam and kinito send secret emails to another, while kinito and jade never see each other but jade is helpful to babysit syrma at anytime.)
Quick sam info: He works for a sea life resort and protects all sea life
Quick jade info: She is a billionaire due to making so many toys, she donates a lot to charity and poor around the world.
Once you interact with VirusKiller!Kinito, he will ask you why you deleted him, and assume it was a mistake. (He is very clingy and desperate for the user to come back, and once they do he may get very pushy and shower you with gifts, tending to follow you around anywhere on your browser.)
(Edited version under photos)



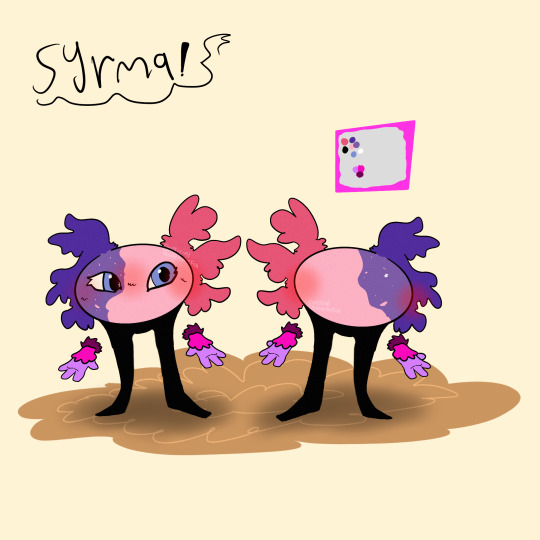

Facts and sillies:
VirusKiller!Kinito is a very, tired and overwhelmed guardian of syrma, always dealing with her,,, special actions,,,
Kinito holds a grudge against the user but hides it very well. He plans one day to get his payback.
Syrma and Kinito HATE their creator, parental issues lmao.
Kinito has 4 monster forms.
Syrma has 2 monster forms.
Syrma has selective mutism around certain people. Syrma also used to have a blind right eye which soon was cured.
Both kinito and syrma are extremely flexible and don't really have "bones" due to being digital.
Syrma usually squeaks around people she trusts, or when she is happy.
Syrma cannot detect viruses unlike kinito, due to her meant to be a virus.
Kinito has BAD anger issues and can physically make the computer overheat.
#officialhunterthefox#fandom#kinitopet#kinito#kinito the axolotl#kinitopetgame#kinitopet sam#kinitopet jade#kinito fanart#kinito my beloved#kinitoohtfversion#kinito au#kinito oc#ohtf.version2.16kinitoau#viruskiller!kinito#heswaitingforyou…
34 notes
·
View notes
Text
Very funny to see "guy breaks security device which inexplicably unlocks everything" in fiction because you'd assume that would be a bad thing to implement, but from personally studying security procedures, it's actually completely in line with the standard.
There's an adage called "Fail Safe." Not "failsafe," two words. If your system is going to fail, you want it to fail in a manner that's safe for the people using it. If your building's key card system goes down, all of the doors will unlock because if the cause of the failure is... idk a building fire, having every single door permanently lock itself is going to kill people.
When it comes to security, specifically cybersecurity in my case, we're advised to design systems that prioritize human life over property and information.
There's an inverse adage that's "Fail Secure" which is for purely digital spaces. Like if a firewall that vets people trying to access a database goes kaput, the entire system is designed to shut off and become inaccessible, because usually not having the data right this moment isn't going to kill someone.
Physical security is "Fail safe." Digital security is "Fail secure."
4 notes
·
View notes
Text
MHA DR-Self Hero Profile

(I'm not an artist but I tried ;~; )

Hero Name: Impulse
Considering MHA's fantastical laws of physics and such, I'm taking some liberties here, I know EMP's don't necessarily work this way :)
Quirk: Electro-Magnetic Pulse (EMP)
I can use and manipulate EMP’s to affect anything that can use or run on electricity to my will. At some point I learn to control biological tissue by manipulating electrical signals in the cells. I can do anything from diagnosing issues in electronics to accessing any information (even the most confidential) as long as it’s on the device or connected to the internet in any way. Firewalls and encryption can take a bit longer to navigate through, but in general are no issue. No trace is left behind; my activities cannot be traced, even if I pull up the information on a computer for others to see. I can interface with tech and view everything in my head, so battery usage in devices is minimal due to there being no need for screens or physical input. Outside electrical sources are not needed to manipulate most objects.
Skills:
Some of these skills are gained and perfected in my time at UA.
Parkour:
Agility and Speed: Enhances my ability to move rapidly through urban environments, chase villains, or reach areas inaccessible by conventional means.
Escape and Evasion: Allows me to evade capture or dangerous situations.
Rescue Operations: Facilitates swift navigation in disaster zones.
Skateboarding: Translates into Hoverboard use
Quick Transportation: Provides a fast and agile mode of transportation, allowing me to cover ground quickly.
Enhanced Maneuverability: Helps me perform sharp turns and evasive maneuvers during pursuits or escapes.
Combat Utility: The board can be used as a tool in combat, either as a weapon or a shield.
Krav Maga:
Self-Defense: Equips me with practical combat skills to neutralize threats quickly and effectively.
Close-Combat Proficiency: Enhances my ability to handle hand-to-hand combat situations.
Situational Awareness: Trains me to remain vigilant and responsive to immediate threats.
Electronics and Programming:
Tech Control: Allows me to interface with and control technology.
Hacking: Enables me to hack into security systems, disable electronic traps, or access critical information.
Repair and Modification: Equips me with the skills to repair damaged tech or modify devices on the fly.
Cybersecurity:
Counter-Hacking: Allows me to defend against cyber-attacks from villains.
Data Protection: Ensures the safety of personal and mission-related data.
Tech Defense: Helps me implement security measures on their own devices.
Neurobiology:
Safe Manipulation: Enables me to manipulate biological electrical signals safely.
Medical Assistance: Provides the knowledge to offer medical aid, such as stabilizing heartbeats or alleviating pain.
Enhanced Strategy: Offers insight into how opponents' nervous systems function, aiding in the development of effective, non-lethal combat strategies.
Tactical Thinking and Strategy:
Mission Planning: Helps me develop effective plans for complex missions.
Adaptability: Equips me to adjust strategies quickly in response to changing conditions or unexpected challenges.
Team Coordination: Enhances my ability to work with and lead teams, coordinating actions and resources.
Leadership and Communication:
Team Leadership: Prepares me to lead teams of other heroes or rescue personnel, making critical decisions under pressure.
Public Interaction: Equips me to communicate with the public, media, and authorities.
Conflict Resolution: Enhances my ability to de-escalate situations and resolve conflicts peacefully when possible.
First Aid and Emergency Response:
Medical Assistance: Allows me to provide critical care in the field, stabilizing injured individuals until they can receive professional treatment.
Disaster Response: Equips me to manage disaster scenarios, providing aid, organizing evacuations, and ensuring public safety.
Self-Care: Enables me to tend to my own injuries during missions.
Support Items:
Smart Visor:
Augmented Reality Interface: Displays real-time information overlay, including maps, data streams, and tactical readouts, directly in the user’s field of vision.
Enhanced Vision Modes: Includes night vision, thermal imaging, and x-ray vision.
Universal Integration: Can connect to any electronic device or network within range.
Communication Hub: Functions as a secure communication device.
Mental Command: Responds to mental commands for hands-free operation.
Insulation: Protects against electronic surges.
Retractable Smart Wires:
Grappling hooks: Equipped with small yet extremely strong and durable grappling hooks that can latch on to most surfaces, or grip to self when wire is wrapped around an object.
Electric Conductivity: Can channel the user's EMP directly through the cables.
Durable and Flexible: Made from a thin high-strength, flexible material that can withstand extreme conditions and physical stress. Made from a Material that while remaining flexible, does not tangle with itself.
Automatic Retraction: Retracts into a compact, portable spool when not in use.
Variable Length: Length can be adjusted as needed, extending up to several yards.
Collapsible Hoverboard:
Folding Mechanism: Folds down from the size of a skateboard deck into a compact, pocket sized form.
Electric Propulsion: Uses a high-efficiency electromagnetic propulsion system for smooth and silent movement, easily controlled by the user’s quirk.
Remote Summoning: Can be summoned to the user’s location.
Stability and Control: Features advanced gyroscopic stabilization for smooth rides over various terrains.
Speed and Maneuverability: Capable of high speeds and sharp turns.
Pocket Tech:
Micro Bugs
Micro Cameras
Micro Drones
Mini Bombs
Costume:
Sneakers:
Shock-Absorbing Soles: Provides superior cushioning to absorb impact during high-speed movements and long jumps.
Conductive Fabric: Allows me to channel EMP.
Magnetic Traction Pads: Ensures superior grip on the hoverboard, maintaining stability.
Lightweight and Breathable: Keeps the feet cool and dry, enhancing comfort and reducing fatigue during long missions.
Reinforced Toe and Heel Caps: Provides extra protection against impacts and enhances durability.
Socks:
Conductive Fibers: Allows me to channel EMP.
Moisture-Wicking Fabric: Keeps feet dry and comfortable.
Compression Zones: Provides targeted compression to support key areas of the foot and ankle, improving blood circulation and reducing fatigue.
Shock-Absorbing Padding: Enhances comfort by absorbing impact and reducing stress on the feet.
Antimicrobial Treatment: Prevents the growth of odor-causing bacteria, keeping the socks fresh and hygienic.
Seamless Construction: Reduces friction and prevents blisters.
Thermoregulatory Properties: Keeps feet warm in cold conditions and cool in hot conditions.
Reinforced Arch Support: Provides additional support to the arch, enhancing stability and reducing the risk of injuries.
Pants:
Durable Fabric: Provides protection against wear and tear.
Conductive Threading: Allows me to channel EMP.
Moisture-Wicking and Breathable: Keeps me cool and dry.
Reinforced Knees and Seat: Provides extra durability and protection.
Flexible: Ensures a comfortable fit that adapts to my movements, providing flexibility and reducing restrictions.
Multiple Pockets: Provides ample storage space for tools, gadgets, and personal items.
Thermoregulatory Properties: Keeps me warm in cold conditions and cool in hot conditions.
Harness:
Durable Material: Ensures the harness can withstand the rigors of combat and daily use.
Ergonomic Design: Provides comfort and support during prolonged wear, distributing weight evenly.
Adjustable Fit: Provides a customizable fit, ensuring the harness stays secure and comfortable.
Attachment Points: Allows me to attach additional gear, tools, or accessories.
Quick-Release Buckles: Ensures the harness can be easily and quickly donned or doffed.
Integrated Power Conduits: Allows me to channel EMP, enhancing my ability to manipulate the smart cables.
Reflective and High-Visibility Elements: Increases visibility in low-light conditions, ensuring I can be seen by allies and avoid hazards.
Shirt:
Conductive Fabric: Allows me to channel EMP.
Moisture-Wicking and Breathable: Keeps me cool and dry.
Compression Zones: Provides support to key muscle groups, improving blood circulation and reducing muscle fatigue.
Reinforced Seams: Enhances durability and prevents tearing.
Thermoregulatory Properties: Keeps me warm in cold conditions and cool in hot conditions.
Flexible and Stretchable: Ensures a snug fit that moves with my body, providing full range of motion and reducing restrictions.
Antimicrobial Treatment: Prevents the growth of odor-causing bacteria, keeping the shirt fresh and hygienic.
Gloves:
Conductive Fabric: Allows me to channel EMP.
Ergonomic Design: Provides a natural fit that reduces hand fatigue and enhances dexterity.
Reinforced Palms and Fingers: Offers extra protection against abrasion and impact.
Touchscreen Compatibility: Allows me to interact with touchscreen devices if needed.
Breathable and Moisture-Wicking: Keeps hands cool and dry by allowing sweat to evaporate quickly.
Adjustable Wrist Straps: Provides a secure fit, ensuring the gloves stay in place.
Shock-Absorbing Padding: Reduces impact and vibration, protecting the hands.
Antimicrobial Treatment: Prevents the growth of odor-causing bacteria, keeping the gloves fresh and hygienic.
Jacket:
Insulated Fabric: Provides superior warmth without adding bulk.
Waterproof and Windproof Outer Layer: Protects against rain, snow, and wind.
Conductive Threading: Allows me to channel EMP.
Heated Panels: Integrated heating elements providing adjustable warmth on demand.
Breathable and Moisture-Wicking: Keeps me dry and comfortable by drawing sweat away from the skin.
Adjustable Hood: Provides additional warmth and protection, and can be removed when not needed.
Multiple Pockets: Provides ample storage space for tools, gadgets, and personal items.
Reinforced Seams and Elbows: Enhances durability and provides extra protection in high-stress areas.
Reflective Elements: Increases visibility in low-light conditions, ensuring I can be seen by allies and avoid hazards.
Stealth Version:
Light-Absorbing Fabric: Reduces visibility by minimizing light reflection.
Sound-Dampening Fabric: Reduces noise generated by movement.
Minimalistic Design: Reduces the risk of snagging or catching on obstacles, ensuring smooth and silent movement.
Hood and Mask: Provides additional concealment.

+1 Brownie point if you read this whole thing :)
#bog is shifting#reality shifting#shiftblr#shifting#shifting realities#desired reality#reality shifter#reality shift#mha dr#mha#my hero academia#bogs mha dr
13 notes
·
View notes
Text
For years, it's been an inconvenient truth within the cybersecurity industry that the network security devices sold to protect customers from spies and cybercriminals are, themselves, often the machines those intruders hack to gain access to their targets. Again and again, vulnerabilities in “perimeter” devices like firewalls and VPN appliances have become footholds for sophisticated hackers trying to break into the very systems those appliances were designed to safeguard.
Now one cybersecurity vendor is revealing how intensely—and for how long—it has battled with one group of hackers that have sought to exploit its products to their own advantage. For more than five years, the UK cybersecurity firm Sophos engaged in a cat-and-mouse game with one loosely connected team of adversaries who targeted its firewalls. The company went so far as to track down and monitor the specific devices on which the hackers were testing their intrusion techniques, surveil the hackers at work, and ultimately trace that focused, years-long exploitation effort to a single network of vulnerability researchers in Chengdu, China.
On Thursday, Sophos chronicled that half-decade-long war with those Chinese hackers in a report that details its escalating tit-for-tat. The company went as far as discreetly installing its own “implants” on the Chinese hackers' Sophos devices to monitor and preempt their attempts at exploiting its firewalls. Sophos researchers even eventually obtained from the hackers' test machines a specimen of “bootkit” malware designed to hide undetectably in the firewalls' low-level code used to boot up the devices, a trick that has never been seen in the wild.
In the process, Sophos analysts identified a series of hacking campaigns that had started with indiscriminate mass exploitation of its products but eventually became more stealthy and targeted, hitting nuclear energy suppliers and regulators, military targets including a military hospital, telecoms, government and intelligence agencies, and the airport of one national capital. While most of the targets—which Sophos declined to identify in greater detail—were in South and Southeast Asia, a smaller number were in Europe, the Middle East, and the United States.
Sophos' report ties those multiple hacking campaigns—with varying levels of confidence—to Chinese state-sponsored hacking groups including those known as APT41, APT31, and Volt Typhoon, the latter of which is a particularly aggressive team that has sought the ability to disrupt critical infrastructure in the US, including power grids. But the common thread throughout those efforts to hack Sophos' devices, the company says, is not one of those previously identified hackers groups but instead a broader network of researchers that appears to have developed hacking techniques and supplied them to the Chinese government. Sophos' analysts tie that exploit development to an academic institute and a contractor, both around Chengdu: Sichuan Silence Information Technology—a firm previously tied by Meta to Chinese state-run disinformation efforts—and the University of Electronic Science and Technology of China.
Sophos says it’s telling that story now not just to share a glimpse of China's pipeline of hacking research and development, but also to break the cybersecurity industry's awkward silence around the larger issue of vulnerabilities in security appliances serving as entry points for hackers. In just the past year, for instance, flaws in security products from other vendors including Ivanti, Fortinet, Cisco, and Palo Alto have all been exploited in mass hacking or targeted intrusion campaigns. “This is becoming a bit of an open secret. People understand this is happening, but unfortunately everyone is zip,” says Sophos chief information security officer Ross McKerchar, miming pulling a zipper across his lips. “We're taking a different approach, trying to be very transparent, to address this head-on and meet our adversary on the battlefield.”
From One Hacked Display to Waves of Mass Intrusion
As Sophos tells it, the company's long-running battle with the Chinese hackers began in 2018 with a breach of Sophos itself. The company discovered a malware infection on a computer running a display screen in the Ahmedabad office of its India-based subsidiary Cyberoam. The malware had gotten Sophos' attention due to its noisy scanning of the network. But when the company's analysts looked more closely, they found that the hackers behind it had already compromised other machines on the Cyberoam network with a more sophisticated rootkit they identified as CloudSnooper. In retrospect, the company believes that initial intrusion was designed to gain intelligence about Sophos products that would enable follow-on attacks on its customers.
Then in the spring of 2020, Sophos began to learn about a broad campaign of indiscriminate infections of tens of thousands of firewalls around the world in an apparent attempt to install a trojan called Asnarök and create what it calls “operational relay boxes” or ORBs—essentially a botnet of compromised machines the hackers could use as launching points for other operations. The campaign was surprisingly well resourced, exploiting multiple zero-day vulnerabilities the hackers appeared to have discovered in Sophos appliances. Only a bug in the malware's cleanup attempts on a small fraction of the affected machines allowed Sophos to analyze the intrusions and begin to study the hackers targeting its products.
As Sophos pushed out patches to its firewalls, its team responsible for threat intelligence and incident response, which it calls X-Ops, also began an effort to track its adversary: Sophos included in its “hotfix" for the hackers' intrusions additional code that would collect more data from customers' devices. That new data collection revealed that a single Sophos device registered in February of 2020 in Chengdu showed signs of early alterations similar to the Asnarök malware. “We started to find tiny little indicators of the attack that predated any other activity,” McKerchar says.
Using registration data and records of downloads of code Sophos made available to its customers, the X-Ops team eventually identified a handful of machines it believed were being used as guinea pig devices for Chinese hackers as they sought to find vulnerabilities and test their intrusion techniques prior to deployment. Some of them seemed to have been obtained by a Chengdu-based company called Sichuan Silence Information Technology. Others were tied to an individual who used the handle TStark, whom X-Ops analysts then found had held a position at the University of Electronic Science and Technology of China, also in Chengdu.
X-Ops analysts could even observe individuals using computers and IP addresses tied to the test devices reading Sophos' online materials that detailed the firewalls' architecture. “We could see them researching us,” McKerchar says.
In late April of 2020, Dutch police worked with Sophos to seize a Netherlands-based server that Sophos had identified as being used in the Asnarök infection wave. In June of that year, however, the hackers launched another round of their mass intrusions, and Sophos found they had significantly reduced the complexity and “noise” of their malware in an attempt to evade detection. Yet through the increased data collection from its devices and the intelligence it had assembled on the Chengdu exploit development group, Sophos was able to spot the malware and push out patches for the vulnerabilities the hackers had used within a week, and even identify a “patient zero” machine where the new malware had first been tested two months earlier.
The next month, X-Ops took its most aggressive step yet in countering the effort to exploit its devices, deploying its own spy implants to the Sophos devices in Chengdu they were testing on—essentially hacking the hackers, albeit only through code added to a few installations of its own products the hackers had obtained. Sophos says that preemptive surveillance allowed the company to obtain key portions of the hackers' code and head off a third wave of their intrusions, catching it after only two customers had been compromised and pushing out a patch designed to block the attacks, while obfuscating that fix to avoid tipping off the hackers to Sophos' full knowledge of their techniques.
“In the first wave, we were on the back foot. In the second wave, it was an even match,” says McKerchar. “The third attack, we preempted.”
A New Phase of the Game
Starting in 2021, Sophos says it began to see far more targeted attacks from Chinese hacker groups exploiting its products, many of which it was able to uncover due to its efforts to surveil the research of the Chengdu-based exploit development network. Over the next two years, the hackers continued hijack vulnerabilities in Sophos appliances in a wide variety of targeted attacks hitting dozens of targets in Asia and the West.
In September of 2022, for instance, Sophos found a campaign exploiting a vulnerability in its products that had breached military and intelligence agencies in a Southeast Asian country, as well as other targets including water utilities and electric generation facilities in the same region. Later, Sophos says, a different Chinese state-sponsored group appears to have exploited a bypass for its patch for that vulnerability to target government agencies outside of Asia, in one instance hacking an embassy shortly before it was set to host officials from China's ruling Communist Party. It also found intrusions at another country's nuclear energy regulatory agency, then a military facility in the same country and the airport of the country's capital city, as well as other hacking incidents that targeted Tibetan exiles.
“We just opened the door on a huge amount of high-end targeted activity, a Pandora's Box of threat intelligence," McKerchar says.
As the hackers' tooling continued to evolve in response to Sophos' attempts to head them off, the company's X-Ops researchers at one point pulled from a test device they were surveilling a unique new specimen of malware: The hackers had built a “bootkit,” an early attempt at malware designed to infect a Sophos firewall's low-level code that's used to boot up the device before its operating system is loaded, which would make the malware far harder to detect—the first time Sophos believes that sort of firewall bootkit has ever been seen.
X-Ops never found that bootkit deployed on an actual victim's machine, but Sophos CISO McKerchar says he can't rule out that it was in fact used somewhere and evaded detection. “We certainly tried to hunt for it, and we have some capability to do that,” says McKerchar. “But I would be brash to say it's never been used in the wild.”
As Sophos has tried to understand the motives of the Chengdu-based network of hackers digging up vulnerabilities and providing them to the Chinese state, that picture has been complicated by the strange fact that the researchers finding those flaws may have on two occasions also reported them to Sophos itself through its “bug bounty” program. On one occasion, for instance, the exact vulnerability used in a hacking campaign was reported to Sophos by a researcher with a Chinese IP address just after it was first used in an exploitation campaign—Sophos paid the researcher $20,000 for their findings.
That bizarre incongruity with the Chengdu-based researchers' apparent role as suppliers of intrusion techniques for Chinese state hacking groups and its bug bounty reports to Sophos, McKerchar argues, show perhaps how loose the connections are between the researchers finding these vulnerabilities and the state hackers exploiting those bugs. “I think this is a security research community which is patriotically aligned with PRC objectives,” he says, referencing the People's Republic of China. “But they're not averse to making a bit of money on the side.”
Contacts at the University of Electronic Science and Technology China didn't respond to WIRED's request for comment on Sophos' report. Sichuan Silence Information Technology couldn't be reached for comment, and appears to have no working website.
Sophos' timeline of its struggle against a highly adaptive adversaries sussing out its products' hackable flaws points to the success of China's efforts to corral its security research community and funnel its discoveries of vulnerabilities to the government, says Dakota Cary, a researcher at the Atlantic Council, a nonpartisan think tank, who has focused on that Chinese exploit development pipeline. He points to China's efforts, for instance, to foster hacking competitions as a source of intrusion techniques for its offensive hacking efforts, as well as 2021 legislation that requires researchers and companies based in China to report to the government any hackable bug they find in a product.
“In Sophos' document, you see the interconnectedness of that system kind of shine through,” says Cary. “The culture of these organizations working together or competing for work, and the way that the government is trying to centralize collection of vulnerabilities and then distribute those tools to offensive teams—you see all of that reflected.”
Sophos' report also warns, however, that in the most recent phase of its long-running conflict with the Chinese hackers, they appear more than ever before to have shifted from finding new vulnerabilities in firewalls to exploiting outdated, years-old installations of its products that are no longer receiving updates. That means, company CEO Joe Levy writes in an accompanying document, that device owners need to get rid of unsupported “end-of-life” devices, and security vendors need to be clear with customers about the end-of-life dates of those machines to avoid letting them become unpatched points of entry onto their network. Sophos says it's seen more than a thousand end-of-life devices targeted in just the past 18 months.
“The only problem now isn't the zero-day vulnerability,” says Levy, using the term “zero-day” to mean a newly discovered hackable flaw in software that has no patch. “The problem is the 365-day vulnerability, or the 1,500-day vulnerability, where you've got devices that are on the internet that have lapsed into a state of neglect.”
That warning was echoed by Cybersecurity and Infrastructure Security Agency assistant director for cybersecurity Jeff Greene, who stresses the risk of Chinese hackers exploiting older, unpatched systems, as well as the broader, ironic threat of network perimeter appliances serving as entry points for hackers. “These edge devices often have inherent insecurities, they’re often not managed once they’re put out, they're not patched," says Greene. “We’ll leave a trail of these devices for a long time that attackers will be looking to compromise.”
Sophos CISO McKerchar says the company is revealing its five-year fight with the Chengdu-based hacking network to amplify those warnings, but also to end a kind of cybersecurity industry omertà around the growing issue of security companies' own products creating vulnerabilities for their customers. “Trust in the industry has been massively eroded in the past few years. There's a huge amount of skepticism across about the way that vendors are handling these risks, but we've relied on silence instead,” says McKerchar. “We want to show a bit of vulnerability ourselves, recognize that we've had problems, then tell the story about how we stepped up.”
8 notes
·
View notes
Text
Escape! (Batmom in DCeased)
Time to run! Reader... did you read the first scene? i hope ya did, you got options! (Scene 1)
As you cradled yourself in the room, you realize that Alfred is somewhere in the manor. Your son Damian with with the Kent’s, Jason is probably ahead of the game and not dead. You cant just sit here! You get up as reach under the bed, you pull out a box that has escape equipment. Rope, a walkie-talkie with a bat symbol on it, and some mini toiletries. You head to the balcony and make sure the rope is secured before carefully descending yourself onto the ground. Once your feet were on the cool grass that’s when you realized that you were still in your night gown.
“Ok, Bruce is with the league. He must know what this is. He has to know what’s happening.”
You ran back inside in the manor and made a B-line to the grandfather clock. When you got in you saw your husband siting Infront of the computer screen. Watching Gotham's citizens tear each other apart. “Bruce!”
You’ve never moved so fast. As soon as Bruce stood from his seat you jumped into his arms. Sharing a deep kiss. Relief washed over you both. But it was only for a moment as the camera angle switched to another shot of the city. You pull back and look into his eyes
“are you ok?” His look of concern rattled you to your core as you remembered what had happened to your sons. You start to whale as you cried in his chest
“Bruce… they’re. Dick and Tim they’ve…”
Bruce closed his eyes and he held onto you tighter. He was too late. That’s when he realized that Alfred was in danger. “This is a virus transmitted through the internet. Computer! are the firewalls active?.”
“Not all of them sir.”
Bruce sucked his teeth “Damn it. EMP the house NOW!”
You held onto him as the manor above grew silent. “Stay here.” Bruce gave you a kiss on your hand before heading up the stairs. You look at the console desk to find a walkie with the bat symbol on it.
“Damian. Can you hear me?” You say in a somber tone. Honestly you didn’t expect an answer given how your other two sons turned.
“Ummi. Is that you.”
You felt your legs shake as you heard your youngest’s voice though the device “yes! Yes baby I’m here. Where are you? Are you safe. Don’t look at screens!” You cram all the important survival information that you’ve learned though sobs and choked laughter.
“Yes mother. I’m with the Kents. Superman has informed us. We’re at the daily planet.” Damian voice was cold yet concerned. You knew that his to the point attitude was a way to protect himself from grief. He probably put two and two together that somethings happened to his family. “Where is my father”
“Bruce went to get Alfred. He’s.” The sound of metal clanking caused you to turn around. To your horror Bruce is in one of Mr. Freezes suites with Alfred holding a shot gun close behind. “Don’t tell me… please don’t tell me you.”
Bruce responded with a curt nod. You look into his eyes, you see his pain. And without another word you pass the walkie to him while you go around the cave seeking out essentials. Two katanas, two hand guns. Smoke grenades. Anything you can carry on the move.
You stop at one of the normal looking spaces in the cave. It was a cozy relaxation space for the family when they came home from patrol. You would suture their wounds or scold them for being reckless in that space.
“I am so proud of you my son. I wish I would be with you see it.” You heard Bruce say his final goodbyes. To his son.
You grab the picture frame and walk to Alfred who stood at the ready. Whats next?
You place a hand over his “let me. Now find Damian. Please.” You take his shotgun.
You take the Batman case and look away as you hear your husbands growl. Gone from this world.
37 notes
·
View notes
Text
OPERATIVE PROFILE
⋘ 𝑙𝑜𝑎𝑑𝑖𝑛𝑔 𝑑𝑎𝑡𝑎… ⋙ 𝐍𝐨𝐰 𝐥𝐨��𝐝𝐢𝐧𝐠. . . █▒▒▒▒▒▒▒▒▒ 𝟏𝟎% ███▒▒▒▒▒▒▒ 𝟐𝟎% █████▒▒▒▒▒ 𝟓𝟎% ███████▒▒▒ 𝟕𝟎% ██████████ 𝟏𝟎𝟎%
REAL NAME: Lila Drilovsky NUMBER: Numbuh 362.2 AGE: 11 GENDER: Female ROLE: Spy / Second-in-Command SECTOR: V.3 CURRENT STATUS: Active
PERSONALITY PROFILE
✅ STRENGTHS: ✔ Master of Stealth – Lila moves unseen, slipping past defenses with surgical precision. ✔ Tactical Genius – Adapts to situations in real-time, making her an invaluable strategist. ✔ Surveillance Expert – Whether hacking security feeds or listening in on enemy chatter, Lila always knows what’s coming. ✔ Cool Under Pressure – Never rattled, even in the most intense situations. ✔ Highly Adaptable – No matter the mission, she finds a way to turn the odds in her favor.
❌ WEAKNESSES: ✖ Emotionally Reserved – Hard to read, making it difficult for teammates to gauge what she’s thinking. ✖ Secretive – Keeps her plans close to the chest, sometimes leaving her squad frustrated. ✖ Lone Wolf Mentality – Struggles to rely on others, taking on too much alone. ✖ Unapproachable Aura – Her quiet intensity can make her seem distant, even when she cares deeply.
⚠ WARNING: Never mistake her silence for inaction. Lila is always calculating her next move—often before you even realize there’s a problem.
SKILLS & ABILITIES
🔹 Stealth & Infiltration – Slips past enemies undetected, whether in broad daylight or deep cover. 🔹 Advanced Hacking – Can breach enemy firewalls, disable alarms, and dig up classified intel with ease. 🔹 Tactical Leadership – Though she rarely speaks up, when she does, her orders are sharp, precise, and effective. 🔹 Observation & Analysis – Nothing gets past her; she picks up on details others miss. 🔹 Covert Communication – Uses encrypted signals and subtle cues to keep her team in sync.
WEAPONRY & GADGETS
S.I.L.E.N.T. (Stealth Infiltration & Logistics Encryption Nano-Toolkit)
Description: A cutting-edge espionage tool designed for hacking, infiltration, and silent communication. Compact and multi-functional, S.I.L.E.N.T. allows Lila to override security systems, scramble surveillance, and relay encrypted messages without a trace. In her hands, it's the ultimate spy device—capable of turning the tides of any mission before the enemy even knows she's there.
CLASSIFIED NOTES
🔐 "Lila doesn’t waste words. When she speaks, listen—she’s already thought five steps ahead." 🔐 "No lock, no code, no system can keep her out for long. If intel exists, she’ll find it." 🔐 "She may not be the loudest in the room, but if she’s watching your back, you’re in the safest hands possible."
FINAL ASSESSMENT
"Lila Drilovsky is the definition of a shadow operative—swift, smart, and always in control. As second-in-command, she’s a vital tactical mind, though her secretive nature keeps even her closest allies guessing. But don’t mistake her silence for indifference; when it matters most, Lila is the unwavering force that keeps her team one step ahead of danger."
<< END OF FILE >>
#codename knd#knd#knd au#knd oc#codename kids next door au#codename#knd 2nd gen#2nd gen#knd ocs#character bio#lila mckenzie#numbuh 136.2
5 notes
·
View notes